Intellectual property has become one of the most valuable assets businesses own, making it a prime target for cybercriminals.

According to Halock Security Labs:
“IP theft causes $600 billion in annual losses to the U.S. economy.”
This figure demonstrates the massive scale of this threat. Iolo Security, in this regard, is of the view:
“Intellectual property theft involves the unauthorized use, reproduction, or distribution of someone else’s creations, inventions, or proprietary information.”
This comprehensive guide explains what intellectual property means in cybersecurity, the threats facing IP, and proven protection strategies.
Source: Halock Security – IP Theft and Cybersecurity
Understanding Intellectual Property in Cybersecurity Context
Intellectual property refers to creations of the mind protected by law, inventions, artistic works, designs, symbols, names, and proprietary information that give businesses competitive advantages. In cybersecurity, IP encompasses the digital assets and intangible property that companies must protect from theft, espionage, and unauthorized access.
Types of Intellectual Property
Patents protect inventions and technological innovations. In cybersecurity, this includes security algorithms, encryption methods, authentication systems, and security software architectures. Patents grant exclusive rights to make, use, or sell inventions for 20 years.
Copyrights protect original works of authorship, including software code, documentation, user interfaces, training materials, and security research publications. Copyright exists automatically upon creation and lasts for 70 years even after the author’s lifetime.

Trademarks protect brand identities, including company names, logos, product names, and slogans. In cybersecurity, trademarks distinguish security products and services in the marketplace, building brand recognition and customer trust.

Trade Secrets include confidential business information providing competitive advantages, proprietary algorithms, customer lists, pricing strategies, security architectures, source code, and business processes. Unlike patents, trade secrets have no expiration if secrecy is maintained.
Why Intellectual Property Matters in Cybersecurity
Intellectual property often represents years of research and development investment, core competitive advantages differentiating companies from competitors, revenue streams from licensing or product sales, and market positioning establishing industry leadership. When IP is stolen, companies lose not just information but competitive edges, market share, and revenue potential.
Source: Iolo – What Is IP Theft
Cyber Threats Targeting Intellectual Property
Cybercriminals, competitors, and nation-state actors use sophisticated methods to steal IP in the following manner:
Advanced Persistent Threats (APTs)
APTs are prolonged, targeted attacks where intruders gain access to networks and remain undetected for extended periods specifically to steal intellectual property. Nation-state actors often conduct APT campaigns targeting defense contractors, technology companies, and research institutions to steal trade secrets and technological innovations.
These attacks involve careful reconnaissance identifying high-value IP, custom malware evading detection systems, lateral movement to access development servers and research databases, and slow data exfiltration avoiding suspicion.
Insider Threats and Employee Data Theft
Halock Security notes that employees, contractors, or business partners with legitimate access pose significant IP theft risks. Insiders might steal IP when leaving for competitors, be recruited by foreign intelligence services, accidentally expose information through negligence, or be compromised through social engineering.
Insider threats are particularly dangerous because perpetrators already have authorized access, understand where valuable IP resides, and can exfiltrate data without triggering typical intrusion alarms.
Ransomware with Data Exfiltration
Modern ransomware attacks do not just encrypt data; they steal it first. Criminals threaten to publish stolen IP, including source code, product designs, and confidential research, if ransoms are not paid. This creates dual pressure even for organizations with good backups.
Supply Chain Compromises
Attackers target vendors, suppliers, or service providers to access multiple companies’ IP through single compromises. Software supply chain attacks compromise development tools or dependencies, affecting all downstream users.
Phishing and Social Engineering
Targeted phishing attacks trick employees into revealing credentials or downloading malware that provides IP access. Criminals research targets on LinkedIn and social media to craft convincing messages referencing real projects and colleagues.
Cloud and Remote Work Vulnerabilities
Intellectual property stored in cloud services or accessed by remote workers creates new attack surfaces. Misconfigured cloud storage, weak access controls, and unsecured home networks provide IP theft opportunities.
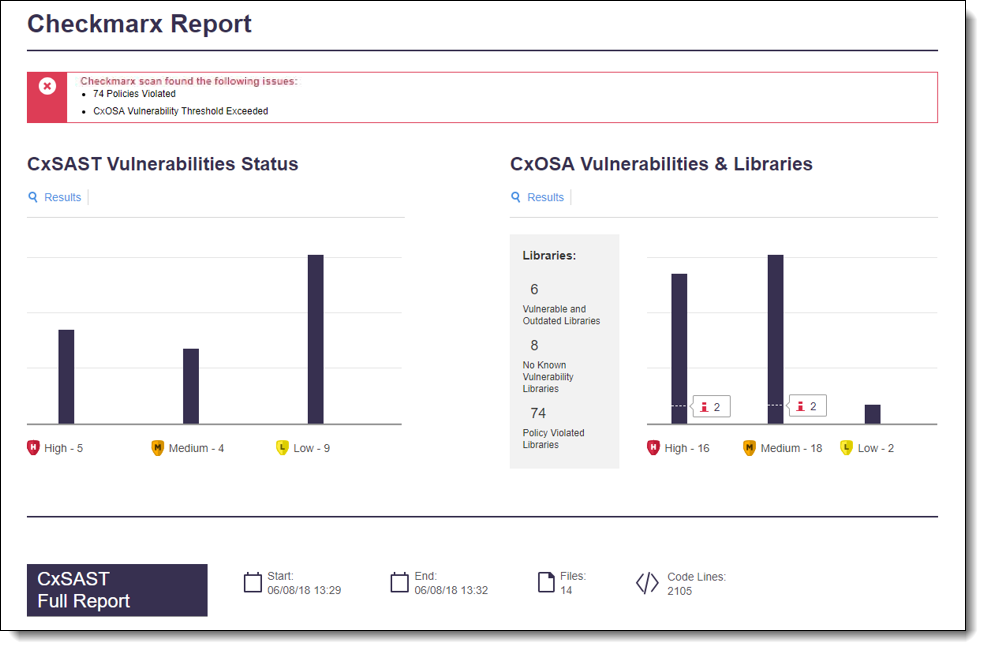
Source: Checkmarx – Securing IP
Protecting Intellectual Property: Cybersecurity Strategies
Comprehensive IP protection requires multiple security layers:
Data Classification and Inventory
Identify and catalog all intellectual property assets including patents, source code, product designs, research data, customer information, and business processes. Classify information by sensitivity level and apply appropriate protection measures based on classification.
Access Control and Least Privilege
Implement strict access controls ensuring employees access only IP necessary for their roles. Use role-based access control (RBAC) limiting permissions by job function, multi-factor authentication for accessing sensitive IP, privileged access management for administrative accounts, and regular access reviews removing unnecessary permissions.
Encryption for Data Protection
Encrypt intellectual property both at rest and in transit. Use strong encryption for databases containing IP, file-level encryption for sensitive documents, encrypted communication channels for sharing IP, and encrypted backups protecting archived IP.
Network Segmentation
Separate networks containing intellectual property from general business systems. Create isolated segments for research and development, secure zones for source code repositories, restricted networks for proprietary databases, and air-gapped systems for extremely sensitive IP.
Data Loss Prevention (DLP)
Deploy DLP solutions monitoring and controlling IP movement. Configure DLP to detect sensitive data leaving the network, block unauthorized uploads to cloud storage, alert on suspicious file access patterns, and prevent email transmission of confidential IP.
Security Monitoring and Anomaly Detection
Implement continuous monitoring detecting unusual IP access or transfer patterns. Monitor for after-hours access to sensitive systems, large file downloads from development servers, unusual data transfers to external destinations, and access patterns inconsistent with job roles.
Secure Development Practices
For software companies, protect source code through secure code repositories with access logging, code review processes before commits, automated security scanning for vulnerabilities, and version control tracking all changes.
Employee Training and Awareness
Train staff on IP protection importance, recognizing social engineering attempts, proper handling of confidential information, and reporting security incidents. Include IP protection in onboarding and conduct regular refresher training.
Incident Response Planning
Develop specific procedures for IP theft incidents including rapid containment to stop ongoing exfiltration, forensic investigation determining what was stolen, legal notification and law enforcement contact, and damage assessment guiding response.
Third-Party Risk Management
Vet vendors and partners accessing IP, require contractual IP protection obligations, limit third-party access to necessary information only, and audit vendor security practices regularly.
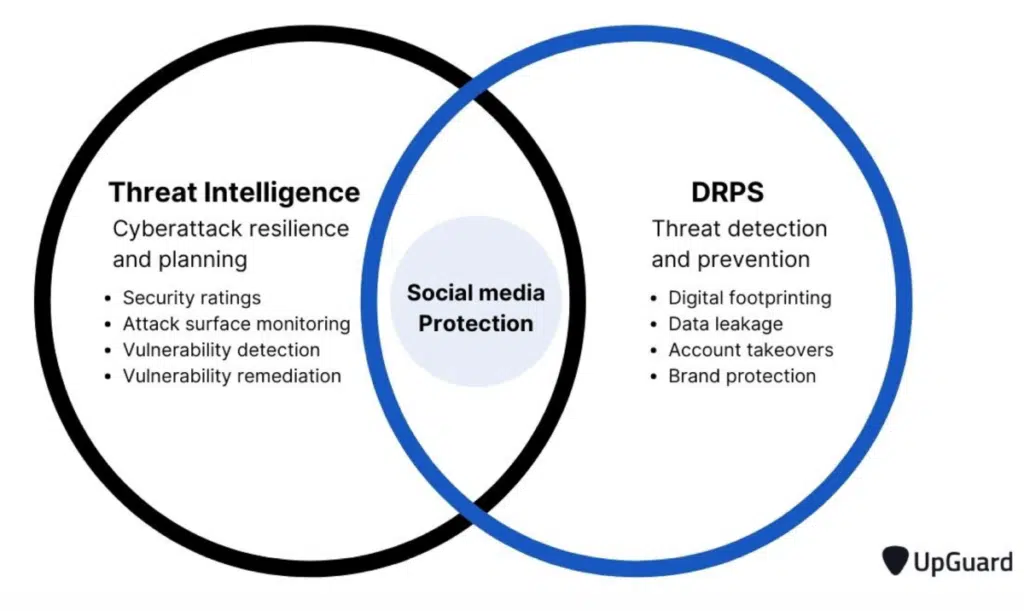
Source: Halock Security – Threat-Intelligence
Legal Frameworks and IP Protection
Understanding legal protections helps enforce IP rights:
Digital Millennium Copyright Act (DMCA)
The DMCA criminalizes circumvention of technological protection measures for copyrighted works and limits liability for online service providers. It provides takedown procedures for infringing content online.
Economic Espionage Act
This federal law criminalizes theft of trade secrets to benefit foreign governments or companies. Penalties include up to 15 years imprisonment and substantial fines.
Defend Trade Secrets Act (DTSA)
The DTSA allows trade secret owners to sue in federal court for misappropriation and provides remedies including injunctions, damages, and attorney fees. It also protects whistleblowers disclosing trade secrets to report violations.
Patent and Trademark Laws
Federal patent law grants exclusive rights to inventions, while trademark law protects brand identifiers. Both provide legal recourse against infringement.
International IP Treaties
WIPO (World Intellectual Property Organization) treaties, the Berne Convention for copyrights, and the Paris Convention for patents provide international IP protection frameworks.
Emerging Technologies and IP Protection
New technologies create both opportunities and challenges for IP security:
AI and Machine Learning
AI helps detect IP theft through anomaly detection and behavioral analysis but also enables sophisticated attacks through automated vulnerability discovery and AI-generated phishing.
Blockchain for IP Management
Blockchain technology provides immutable records of IP creation and ownership, transparent licensing and royalty tracking, and proof of prior art for patents.
Zero-Trust Security
Zero-trust architectures enhance IP protection by continuously verifying all access requests, eliminating implicit trust assumptions, and segmenting access to IP assets.
Conclusion
Intellectual property represents critical business assets worth protecting with robust cybersecurity measures. With IP theft causing $600 billion in annual losses to the U.S. economy, organizations cannot afford to neglect IP protection. Understanding that IP encompasses patents, copyrights, trademarks, and trade secrets, each requiring specific protections, helps organizations develop comprehensive security strategies.
Cyber threats targeting IP range from advanced persistent threats and insider risks to ransomware, supply chain compromises, and social engineering. Protection requires multiple layers including data classification, access controls, encryption, network segmentation, DLP, monitoring, secure development, employee training, incident response, and vendor management.
Legal frameworks including DMCA, Economic Espionage Act, and DTSA provide recourse against IP theft while emerging technologies like AI, blockchain, and zero trust architectures offer new protection capabilities. By implementing the strategies outlined in this guide and maintaining vigilance against evolving threats, organizations can protect their intellectual property from cybercriminals while maximizing the value of their most critical intangible assets.
Frequently Asked Questions
What is the difference between intellectual property and physical property in cybersecurity?
Physical property refers to tangible assets like servers and devices that can be physically secured. Intellectual property is intangible ideas, designs, code, and information that exist digitally and can be copied instantly without physical theft. IP theft is harder to detect because the original remains while copies are stolen. Protecting IP requires different strategies focusing on access control, encryption, and monitoring rather than just physical security.
How can small businesses protect their intellectual property without large security budgets?
Small businesses can protect IP cost-effectively through: implementing strong access controls and multi-factor authentication (often free), using encryption for sensitive files and communications, training employees on IP protection and social engineering awareness, conducting regular backups with offline copies, implementing basic network segmentation, using cloud services with strong security features, and establishing clear IP handling policies. Many effective security measures require process changes rather than expensive technology.
What should I do if I discover my company’s intellectual property has been stolen?
Immediately: contain the breach by isolating affected systems, preserve evidence for investigation, notify your legal team and law enforcement (FBI for significant theft), document what IP was accessed or stolen, assess ongoing threat and close vulnerabilities, notify affected customers or partners if required, and consider legal action against perpetrators. Time is critical, rapid response can limit damage and improve recovery chances.
How does intellectual property theft differ from general data breaches?
General data breaches steal any information, including customer data, credentials, or operational data. IP theft specifically targets valuable proprietary information, providing competitive advantages trade secrets, source code, product designs, research data, and business strategies. IP theft is often more targeted, conducted by sophisticated actors, motivated by competitive or nation-state interests, and has long-term business impacts beyond immediate data loss. Recovery involves competitive damage assessment and legal action to prevent IP exploitation.
What role do employees play in protecting intellectual property?
Employees are both the greatest vulnerability and strongest defense for IP protection. They must understand which information is confidential IP, follow access control and handling procedures, recognize and report social engineering attempts, use secure methods for sharing IP, maintain confidentiality after employment ends, and report suspected IP theft immediately. Organizations should provide comprehensive training, clear policies, secure tools for IP handling, and culture emphasizing IP value and protection importance.
